Reference:
Security in C++ - Hardening Techniques From the Trenches - Louis Dionne - C++Now 2024
https://libcxx.llvm.org/Hardening.html
BCE (bounds check elimination)
https://en.wikipedia.org/wiki/Bounds-checking_elimination
Types of memory safety (as of 2024)
- Spatial memory safety(*)
- Temporal memory safety(*)
- Type safety
- Guaranteed initialization
- Thread safety
Spatial memory safety
- Each memory allocation has a given size.
- Accessing memory out of bounds is called an out-of-bounds(OOB) access.
Temporal memory safety
- All memory accesses to an object should occur during the lifetime of the objects' allocation.
- Access to the object outside of this window is called a use-after-free
Type safety
- A memory allocation is used to represent an object of a particular type.
- Interpreting it as an object of a different type is called a type confusion.
Guaranteed initialization
- When memory is allocated, it contains garbage
- Using that undefined content can lead to information disclosure
- Can also be exploited if the attacker controls the 'garbage'
Thread safety
- concurrent accesses to memory
- data races
C++
- It turns out that most safety issues are technically UB.
Library UB
- UB is what happens when the standard doesn't guarantee anything.
- Beware of precondition.
UB is a specification tool
- creates a contract with the programmer
- allows writing simpler APIs that make sense
- gives freedom to the implementation
Valid strategies:
- do nothing.
- trap if precondition is violated
- log and continue
- ...
Standard library hardening
- turn select UB into guaranteed traps
- provide hardening modes with high-level semantics
- allow users to select hardening mode
- allow vendors to select the default mode
- Not for debugging
- should be shipped as it is
libc++ hardening modes
- none
- fast -> trap
- extensive -> trap SIGTRAP(5)
- debug -> abort verbosely
Hardening mode can be selected in each TU.
ABI considerations
- Orthogonal to hardening
- ABI is a property of the platform
- Vendors can select the desired ABI
- users can't control that
- Huge simplification
- WebKit uses hardened libc++
- Chrome and Google Cloud network virtualization stack.
Clang++
-Wunsafe-buffer-usage
Enter Contracts
- enforcing existing preconditions
- Contracts provide a framework for expressing them
Typed memory operations
- Most temporal memory safety exploits require some type confusion. If memory is never reused for a different type, confusions are impossible.
- Segregate allocations by type!
- Introduced in the Darwin Kernel.
- Data must not alias pointers.
- Randomize buckets on boot.
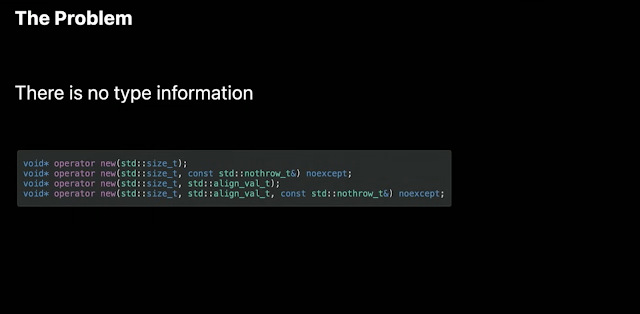
No type info; only size of the type.
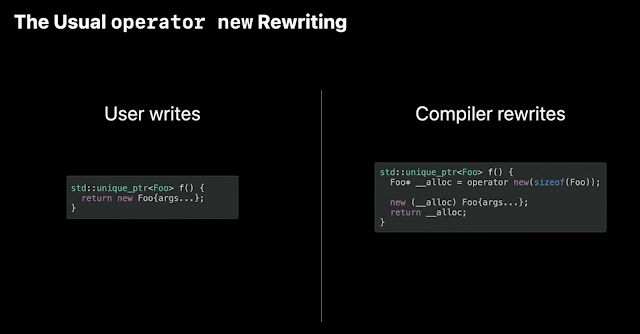
What about user define new operator?
Would be an ABI breaker, but...
(Hey, remember, "all problems in computer science can be solved by another level of indirection")














No comments:
Post a Comment
Note: Only a member of this blog may post a comment.